So I ran into a slight problem while I was trying to access a vendor database that was running SQL Server 2000 Desktop Engine (MSDE). This database contained employee information that we wanted to use in automated batch jobs, hence why not just connect to it and access thed data in real-time and do what we needed to do.
Alas, due to draconian policies from the vendor, the program actually removes the Builtin\Administrators group and customises the SA login during installation and forces me to use their front-end to do anything with the data. (It’s my data….why can’t I access and use my data???….but I’ll save that for another post…)
Although there are many approaches to accessing a SQL Server 2000 / MSDE based system, the “disgruntled” side of me decided that I was going to find out exactly what the SA password is! (Although not my original intent, I guess this method would also work for people who have forgotten their SA password or password to any SQL login).
To do this, I wanted to explore the memory dump of the SQL engine and see what I could find, as Microsoft didn’t necessarily ramp up their security until SQL 2005. I used the following tools:
- ProcDump – a utility mainly used in triggers/batch jobs to generate crash dumps in certain scenarios
- Strings – a utility used to find UNICODE or ASCII strings in a given file
Once you have the tools, perform the following steps:
- First, we need a session in memory, so I opened up the application and logged in. (By default the application accesses the SQL Server by the SA login).
- Then on the server where the SQL Server is running, I opened up a command line window and ran ProcDump with the -ma flag (writes all process memory immediately)
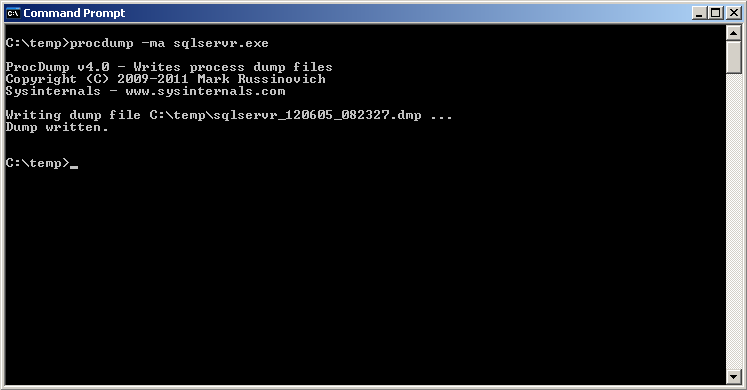
- Once the operation is complete, you will have a dmp file that is filled with unreadable binary information as well as potentially readable strings. Hence we run the Strings utility to pull out all the readable strings.

- Now you have file that you can open up in your favorite text reader. Once it is opened, look for a string with the following format: <servername>sa (ex. TESTBOXsa).

- So from my example, the password for TESTBOXsa is: 2449afwjWclpcms04#93f$a9g234394
(imagine using a brute force cracker for that………yikes!)
As I said before, although it wasn’t my original intent, by using this method you can retrieve the password for any of your SQL logins that are currently in session. This might only work for SQL Server 2000, as I wasn’t successful in using this method for another database from this vendor who has upgraded to SQL Server 2005 Express Edition.
Discussion
Trackbacks/Pingbacks
Pingback: No SA Password, Removed BuiltinAdministrator, No Problem (Part 2) « The Thin Blue DBA - June 6, 2012